Organizations
Hitting the Road After COVID-19: Navigating Cyber Risk While Traveling

Businesses are preparing to enter a brave new world defined by a post-COVID-19 operating environment. With countries lifting different restrictions in phases to promote risk mitigation, organizations and individuals are turning their attention to a part of life that has been highly affected by the pandemic: travel.
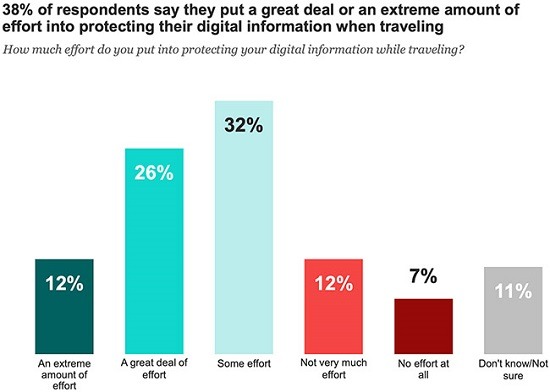
Commerce across the globe has been influenced by travel limitations and now is the time when organizations can once again begin to send their employees overseas for work purposes. In 2019, IBM Security surveyed audiences to assess the level of effort individuals spent protecting their information, and the results weren’t promising. Approximately 62% of respondents said they put none to some effort into protecting their digital information when traveling.
Businesses must stay on top of cyber risk management while employees work from home, as well as when they begin working on the road once again. Even though the work is still remote in nature, the cyber risks involved can be very different. Here are some best practices for senior management and jetsetters alike, to help navigate around cyber security risks and practice cyber risk management when getting back on the road.
Location, Location, Location
Cybersecurity risk management plans begin prior to your departure. You can assess the cyber security risk of travel based on the geopolitical conditions of your destination. According to RedZone Technologies, what you can count on when you land in China is that your phone will be electronically hijacked immediately for SMS (text) and SMTP (email).
Additionally, connecting to Wi-Fi networks available on foreign airlines, airports, and hotels automatically poses a security threat to sensitive information you plan to carry or deliver. Coordinate with your managers during the travel approval process to implement additional measures needed based on your specific destination. These include (but are not limited to) copying and pasting passwords saved on a company-issued USB drive to avoid keylogger malware from stealing credentials or using a burner phone that has limited personal and corporate information on it. Proper research and planning are the foundations to the successful cyber security risk assessment of your potential travel destination.
Preparing for Your Trip: Travel Safety Essentials
Clean clothes? Check. Entertainment for the flight? Check. Enough snacks to last for the whole trip? Check. While you run through your packing checklist, make sure that securing your electronic devices is a top priority.
Take specific risk management measures such as:
- Patching all programs with the latest updates
- Enabling multifactor authentication where possible
- Backing up your devices to secure servers
Physical security strategies include:
- Locking your computer when not in use
- Using combination locks to deter device theft
- Installing privacy screens to thwart prying eyes
These healthy habits are part of a checklist that not only protects sensitive corporate information, but your personal information as well.
Even Free Wi-Fi Has a Price
Have you ever heard the phrase, “There is no such thing as a free lunch?” This applies to travelers who readily use free digital resources such as public Wi-Fi networks and charging stations in airports, planes, or hotels.
An essential way to stay vigilant while traveling is to use your company’s virtual private network (VPN) when connecting to an unknown network. If you are looking for a VPN solution check out CNET’s directory of the top VPN services in which ExpressVPN is highlighted as the Editor’s Choice for speed and proven privacy.
In addition, performing business activities that involve confidential and proprietary information, as well as engaging in sensitive personal activities, such as banking transactions, can pose a cyber security threat. Although USB charging ports are widely accessible in all major airports and hotels, these ports can be compromised and record your screens while in use. To mitigate this inherent risk, travel with your own power adapter outlet or power brick to safely charge devices.
An advanced example of spyware and malware is the Darkhotel threat. According to Kaspersky’s Lab, it appears to be a combination of spear phishing and dangerous malware designed to capture confidential data. Their Darkhotel infographic shows how Darkhotel attacks work in collecting data.

Safe Travels: Secure Your Data While on the Road
Travelers must always be on the lookout for threats of all kinds. When you represent your organization abroad, you are charged with securing all data and proprietary information that accompany you on your journey. You can practice cyber risk mitigation during harmless activities, such as walking from your hotel to the local coffee shop. Turn off auto-connect to Bluetooth devices and Wi-Fi networks, as well as automatic updates for applications. Avoid sharing trip details or sharing your location, both for your own privacy and physical safety.
Home Sweet Home: The Final Leg of Security
When your journey ends and you make it home, remember that your cybersecurity risk management strategy is not over. Just as travelers can pick up foreign pathogens, your electronic devices are also susceptible to carrying bugs homeward.
- To ensure that you protect yourself and the organization you represent, first conduct a full scan of your computer using malware and antivirus software.
- Additionally, you can update the virus definitions and software for the antivirus to run the scan a second time for further safety measures.
- Following this step in the cyber risk management process, you may update all other applications as well.
- Another best practice is to change your passwords for all system accesses just in case your devices were unknowingly compromised.
CISA’s security tip on choosing and protecting passwords includes the following advice: “Programs called password managers offer the option to create randomly generated passwords for all of your accounts. You then access those strong passwords with a master password. If you use a password manager, remember to use a strong master password.”
Conclusion
Cybersecurity risks are an inherent part of the business world. When it comes to travel and international commerce after COVID-19, new challenges will present themselves, including threats from adversaries who want to take advantage of the worldwide pandemic effects.
In the digital age, ensuring your safety and privacy also means protecting your information. While the measures outlined above can reduce your exposure to cybersecurity threats, you must also remain vigilant as cyber challenges may appear during the shift from working at home to working on the road.
As your organization evolves its practices and once again opens the door to travel, make sure you have incident response plans in place and that you communicate cybersecurity risk management strategies to all levels of your company. The expectation is to stay healthy and safe as borders reopen. This advice extends to your data and information as well.
Have Questions or Concerns?
Do you have any questions regarding cyber liability and technology risk management and how your business may be adversely affected? If so, reach out for a free consultation with a Clements cyber risk expert who can explain the risks your business may face and how you can address and mitigate potential issues.
Read this cyber-risk guide to help you become cyber resilient.
Trading One Virus for Another: A COVID-19 Cybersecurity Risk Management Guide
COVID-19 has created a multitude of opportunities for the cyber-crime industry—phishing scams, malware, to name a couple. Read this cyber-risk guide to help you become ready and cyber resilient.
Relevant Helpful Resources
Find tips, trends, and perspectives to help you confidently make decisions and navigate challenges internationally with peace of mind. Read how you can live, operate, and manage risks abroad.
How to Protect Your Nonprofit’s Board of Directors with D&O Insurance
Board members make important strategic and financial decisions for the organizations
Global Business Risk Index
A New Way to Understand Exposure In a world where risk
Employer Liabilities for COVID Vaccines: Duty of Care & Issues to Consider
The consequences of COVID-19 have been felt at every level of