Organizations
Trading One Virus for Another: A COVID-19 Cybersecurity Risk Management Guide

There is no doubt that COVID-19 has created many challenges for individuals and businesses alike. For those lucky enough to maintain employment, personal and work lives have become more intertwined than ever before. In addition to being employees, we have had to become at-home nurses, teachers, barbers, and chefs. With these challenges, however, have come many opportunities and positive outcomes.
Cybersecurity Gaps and Increased Risks for Businesses
Enterprises have recognized the immense impact that technology can have on the way we do business, allowing almost anyone to work from anywhere (in most cases, from home). Many businesses were ill-prepared to face this new reality but responded quickly to ensure they can continue their course of work. Nonetheless, this quick evolution comes with inherent risk. The cyber-crime industry is booming, taking full advantage of the potential gaps in cybersecurity that are resulting from this new normal. Virtual crimes are silently waging cyberwarfare in the background while most of us are busy with our day-to-day routines. These cyberterrorists work similarly to the world’s most resilient businesses, investing their money into new ways to further crime initiatives and legitimize their own enterprises. In the wake of COVID-19, many new and old cyber exposures are more apparent now than ever before.
In their 2020 State of Malware report, Malwarebytes noted “that cybercriminals nowadays are less fixated on singular industries, but more on their victims’ relatively vulnerability and ability to pay up”, and found the following industries to be most affected by cyber threats:
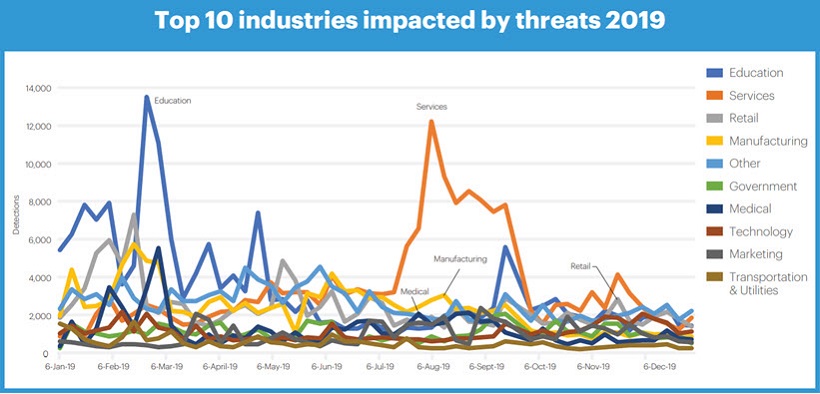
A Guide to Cyber Risk Management
To understand what is going in our digital ecosystem during this health crisis, here is a high-level cyber risk management guide to help you navigate these turbulent times.
1. Phishing Scams
There are several types of phishing scams that have become more evident in the wake of COVID-19, but by no means are new threats. They have taken advantage of mostly behavioral nuances and are the epitome of social engineering.
SMS Phishing:
SMS phishing has largely been effective because of the impulsive behaviors that mobile computing and push notifications have created. SMS schemes usually entail a financial incentive to lure users into clicking embedded links in their messages. This often leads to websites that request information, including but not limited to, names, addresses, telephone numbers, and most importantly, banking information. These scams will certainly increase as more government sponsored aid packages increase. It is best to remember that, unless otherwise broadcasted, there are no governmental entities that would be reaching out via SMS to request information in order to disperse payment.
What can be done?
It is best to limit exposure due to behavioral tendencies. This may mean avoiding the temptation to immediately open texts that you are not expecting, or that are from phone numbers you do not recognize. Additionally, many cell phone models offer the ability to disable push notifications for text messages, even temporarily. The best part is, in addition to limiting your cyber risk, you may even get a little bit more work done without the distractions of notifications!
Phishing for Credentials:
Sticking to taking advantage of psychological predispositions, most phishing emails have very attention-grabbing subject lines that instill a sense of urgency in the recipient. After panic clicking the email upon reading the subject line, the emails and messages people are at risk of opening typically contain just enough information to presume legitimacy. However, often times, phishing emails will ask users to provide additional information, with the catch being, that usually there is still not enough to resolve or give the information the user is hoping to gain from reading the email. There could be a link that would direct them to a login page (which also seems legitimate) in order to proceed. After “logging in,” the user has unknowingly handed their credentials over to the malicious actor. This poses a potential cybersecurity risk for businesses when the email comes from a “trusted internal source.” It is a chance to gain credentials for single sign-on to potentially execute more complex digital crime activity, including but not limited to accessing personally identifiable information or confidential third-party corporate information.
What can be done?
Staying vigilant and having a sober-minded approach to how you handle urgent emails is important. Look for nonsensical grammatical mistakes; hover over links to see if the URLs contain hints that the destination is illegitimate and double check the address where the email is being sent from. If you are still left with suspicion after analyzing the general contents of the email, do not hesitate to pick up the phone and call the person or agency that sent the email to you. Enabling multi-factor authentication (i.e., a method that verifies a user’s identity by requiring various credentials) is something that is already available on many applications, but many users fail to setup.
Phishing with Malicious Content:
Using the same core building blocks of phishing for credentials, some threat actors prefer to inject malware into their victims’ systems instead of simply trying to gain their credentials. This is usually accomplished by attaching a file such as an Excel spreadsheet, and utilize scripting called macros that work behind the scenes to open your system up to malware. After downloading an initial Trojan (digitally similar to the Trojan Horse that the Greeks built), that Trojan will then turn around and download additional types of malware. One such example is ransomware, which can lockdown your system or block you from accessing files until a ransom is paid. In October, 2019 the FBI issued an alert about the increase of high-impact, sophisticated ransomware attacks across all sectors.
The 2019 Symantec Internet Security Threat Report found that cyber crime groups continue to prefer using macros in Office files:
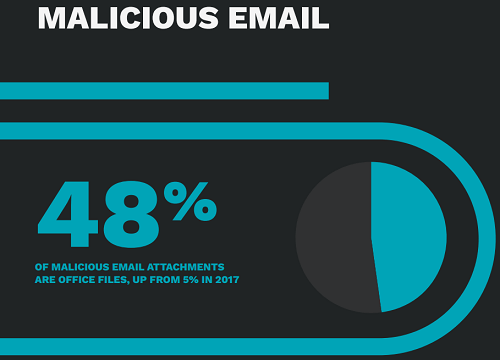
What can be done?
Aside from many of the aforementioned best practices, ensuring that your systems (i.e., applications and security technologies) are current with all available patches and updates is something that you can already do without spending money on protection. Executing these updates as they become available is your best bet in limiting exposure.
2. Malware Distribution
There are plenty of ways malware can be distributed during these trying times in addition to the method mentioned above. Cyber adversaries are continuing to take advantage of the public’s need for health updates and information. Emails from “trusted” sources purporting to be the World Health Organization (WHO), government officials, and local health systems often include links to websites, which can prompt individuals and organizations alike to download malicious software.
Historically, healthcare institutions and facilities have been targeted by ransomware, and according to Health Care Security Report by Corvus, ransomware attacks increased by 350% in Q4 2019 year over year. Recent events relating to COVID-19 and global supply shortages are a golden opportunity for threat actors to send emails including attachments with malicious pictures, PDFs, and Excel spreadsheets of the supplies they can offer to these facilities.
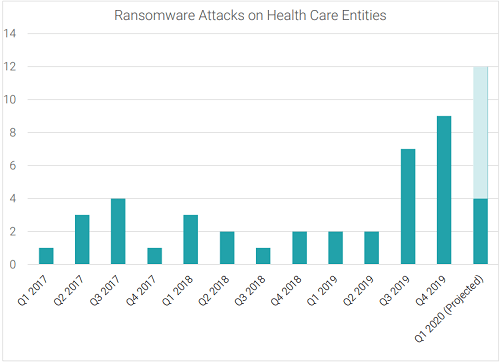
What can be done?
The unfortunate fact is that despite what system protections you have in place, there is no substitute for the “human firewall.” This is the concept that individuals themselves are as valuable of a security asset as technologies are in this world. Whether you are an individual or a business, there are many free resources that give excellent training on how to spot email scams, and a plethora of vendors that offer technological solutions to help combat phishing emails. Having adequate security awareness training for yourself and employees is a step in the right direction.
Traveling opens a whole other world of cyber risk, and following some of the best practices we mapped out in our Navigating Cyber Risk While Traveling article can help prepare you when you hit the road the next time.
3. Malicious Domain Registrations
Cyber adversaries are among the most resourceful and creative criminals on the planet. They employ many techniques that establish their business facades to cover their tracks. One such method is registering domains that could lead individuals to believe that the website they are visiting is legitimate. A domain is the web address that you type into your browser’s URL bar to navigate to a particular website (e.g., www.clements.com). Remember reading that one of the best practices mentioned above in regard to hovering over a link and seeing the web address that populates? Unfortunately, due to falsified domain registrations, it is that much harder to identify whether the website is legitimate. Many cyber criminals are buying domains that have “COVID,” “health,” or “disease” in the names to give the appearance of a trusted website. Some actually use search engine optimization techniques, so that if you search the web for health-related information, their website might even pop up in your results.
Over 70% of newly registered domains were found to be “malicious” or “suspicious” in an analysis by Unit 42 of Palo Alto Network.
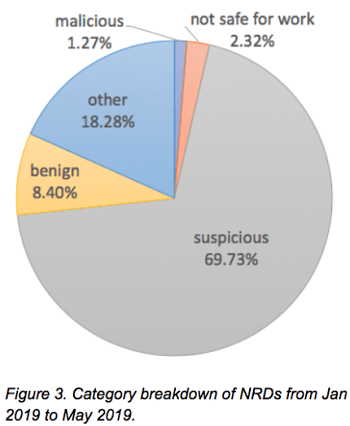
What can be done?
Remember, just because you search or look up something on the web does not mean it is safe to navigate to. You should always cross-check the domains with the website an email is pretending to be. For example, if someone from WHO is sending you an email with an email address of “xxxxxxx@covidinfo.org,” then you should not click any links, or even consider this to be a real email (for the record, WHO’s website is www.who.org).
4. Exploitation of Teleworking Infrastructure
The exponential increase in teleworking in a short period of time is bound to come with ramifications. Zoom teleconferencing software, for example, is one of the most widely adopted tools for conducting remote meetings. Without thinking much about it, millions of hosts and businesses have employed the software without even adding a password to their meetings. This enables anyone with a meeting link to join the meeting with zero resistance. Those super-secret mergers and acquisitions meetings could end up with disastrous circumstances, or that person in the IT department that never responds to your business units’ ticket requests can hear you badmouthing him in your weekly department meetings. Many individuals have been forced to use their personal devices to conduct business—let us hope they have as much great cyber hygiene on these devices as they would on their professional ones. Who knows what malware already existed on their computer before you needed them to work from home?
What can be done?
Make sure enterprise-wide virtual private networks are being used, and that they are fully patched. Update your incident response plans to include the changed workforce distribution. Those emails you are sending out that highlight personal hygiene as being great productivity boosters should include best practices for cyber hygiene. It would be worth surveying your employees using their personal devices, and buying them the proper software protections (e.g., antivirus applications) to better protect them and your business from malware.
5. When All Else Fails — Risk Mitigation
Establishing written policies and procedures, such as incident response plans and business continuity plans to mitigate impact of incidents, is the cornerstone of conducting business in a digital ecosystem. The Clements Worldwide Risk Index provides consumers and risk managers a barometer to validate current thinking on institutional risk by gathering top concerns from clients around the world.
There are always financial and reputational consequences that can result from a data breach. Having scalable and quick-to-implement risk management solutions are more important than ever to establish cyber resilience. One such solution is Cyber and Privacy Liability insurance coverage—insurance for when your business has a cybersecurity breach (digital peril) or privacy breach (possibly a digital or nondigital peril). The costs to rehabilitate your systems and reputation can accumulate thousands of millions of dollars in forensics, legal, and regulatory fees. Conducting cybersecurity risk assessments, owning comprehensive system protections, and having proper insurance coverage can give you a holistic risk management posture to protect you under most dire circumstances.
Have Questions or Need Help?
Do you have any questions regarding cyber and technology risk management and how your business may be adversely affected? If so, reach out for a free consultation with a Clements cyber risk expert who can explain the risks your business may face and how you can address and mitigate potential issues.
Relevant Helpful Resources
Find tips, trends, and perspectives to help you confidently make decisions and navigate challenges internationally with peace of mind. Read how you can live, operate, and manage risks abroad.
How to Protect Your Nonprofit’s Board of Directors with D&O Insurance
Board members make important strategic and financial decisions for the organizations
Global Business Risk Index
A New Way to Understand Exposure In a world where risk
Employer Liabilities for COVID Vaccines: Duty of Care & Issues to Consider
The consequences of COVID-19 have been felt at every level of